Xiid Zero Knowledge Introduction
Despite the rise of zero trust, cyberattacks on enterprise networks and critical infrastructure are more frequent, costly, and damaging then ever.
It's clear that something better is needed.
Xiid delivers a new networking architecture that meets and vastly exceeds the NIST Zero Trust Tenets through the following:
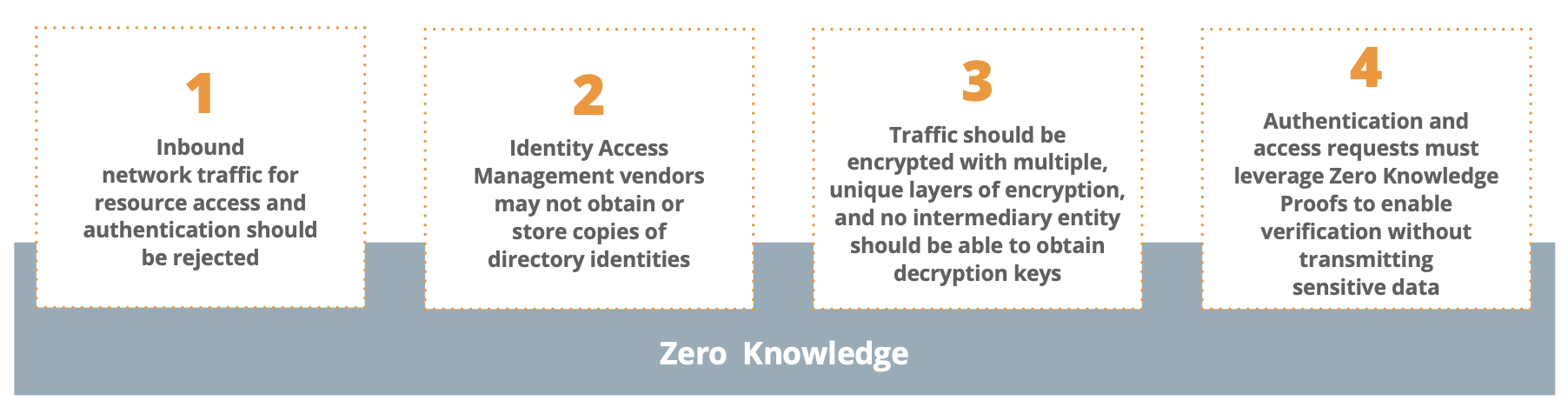
- Open inbound ports are never used, even when instantiating a connection, eliminating network attack surface
- All traffic is wrapped in three layers of quantum-secure encryption, with no intermediary able to decrypt traffic
- Zero Knowledge Proofs authenticate users without transmitting sensitive information or credentials
- All parties – including endpoints and the Zero Trust vendor in-between – are guaranteed to have no excessive knowledge of each other’s sensitive data or location
This documentation details the installation, configuration, and operation of Xiid's product offerings, as well as a guide for deploying a sandbox environment that can be used for testing and to gain familiarity with Xiid.
Click for a metaphorical description of how Xiid's architecture works!
To explain how Xiid's ZKN works from a birds-eye view, let's use a basic postal service as a metaphor.
You are writing a letter to your friend.
When you send the letter in the mail, you must provide the physical address of your friend as well as their name, in case multiple people live at the same address.
The knowledge of your friend's physical address, if shared with others, could be used for nefarious purposes, such as by a burglar that intends to break into your friend's house. To protect that address, you and your friend instead agree on a mutual secret location where you will leave the letter, hidden from view by anyone that may wander by.
You leave the first letter there.
After picking up the letter, the friend writes a response and delivers it to the same location, where you can come by and pick up his response.
In case anyone does manage to find your letters, they'll be unable to read them, since you and your friend use a secret code for all of your letters that only the two of you can decode.
This is how the Xiid STLink software works in conjunction with the Xiid Connector. The Xiid Connector acts as a secret location where end-to-end, quantum-secure encrypted messages can be safely deposited and withdrawn by another STLink running on the authorized endpoint with the decryption keys.
Because of the secret location you and your friend agreed upon, neither of you ever needed knowledge of the other's physical address nor any personal information, other than where to leave the messages.
This is how Xiid's architecture works.
Xiid Products
INFO
Version 4 of Xiid's Identity Access Management platform is in development and documentation for it will be released soon.
| Product | Description |
|---|---|
| SealedTunnel™ (ST) | SealedTunnel™ is Xiid's resource access solution that delivers triple-encrypted, quantum-secure, outbound-only secure tunnels without resources ever needing to accept inbound network traffic or have public IP addresses. |

