Using the Sandbox
What You Can Do
At a minimum, your Sandbox contains a Domain Controller and an RDP Instance.
While configuring these various pieces of the Sandbox, you'll likely need the following key information on the Sandbox infrastructure, including basic usage instructions and the default user account names and passwords.
Domain Controller
Information
The Sandbox Domain Controller comes pre-installed with a number of users and groups in Active Directory. We encourage you to create any users and groups that you wish, as Xiid has only provided basic defaults.
TIP
Although the Sandbox infrastructure should never be used in production, Xiid highly recommends that you change the passwords associated with all users on the Domain Controller for maximum security.
What Is the Domain Controller?
The Domain Controller is an out-of-the-box Windows 2019 Server.
The Domain Controller has had Active Directory Services installed and has been promoted to a Domain Controller as a new domain forest.
The domain name is sandbox.local.
The Domain Controller is not a DNS Server. If you would like to promote your Domain Controller to a DNS server, you can do so after deploying the Sandbox Domain. Be aware that you will need to reconfigure your DHCP Options Set in AWS and you will need a domain name from a trusted Certificate Authority.
Users
There are a number of users created by default in the Sandbox Domain.
| User | Description |
|---|---|
sandboxadmin | The administrator account for the Sandbox Domain |
sandbit | Short for SandboxIT, this is an example IT User on your domain, who may need access to an RDP instance not available to the broader company |
sandboxengineer | Example engineer User on your domain, who may need access to a shared VS Code repository on an RDP instance |
sandboxuser | Example of a general user on your domain, only in the SandboxAll Security Group. |
The sandbit, sandboxengineer, and sandboxuser accounts are disabled by default and passwords are not provided. To use these users, open Active Directory Users and Computers, re-enable each account, and set a password for them.
Groups
A few basic Security Groups are created for you and the users listed above are organized into these basic groups to facilitate access management examples.
| Group | Description | Members |
|---|---|---|
SandboxAll | Security Group for all users in the sandbox OU | sandbit sandboxengineer sandboxuser |
SandboxEngineering | Example Security Group for an Engineering Organization, recommended to use with the VS Code application utilizing the RDP App Application in the Xiid Agent Management Portal | sandboxengineer |
SandboxIT | Example Security Group for an IT Organization and a useful group for demonstrating restricted RDP access to IT | sandbit |
Usage
Here is how to access your newly-deployed Domain Controller:
Windows
Navigate to the AWS EC2 Console, find your Domain Controller, and copy the Public IPv4 Address.
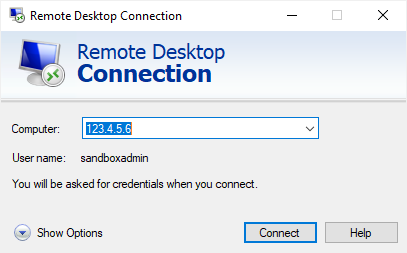
Paste the IP Address into an RDP connection file (.rdp) or into the RDP application of your choosing.
There is also a domain_controller.rdp file available to use in the Sandbox Tools. Right-click the file in Windows File Explorer, click Edit, enter the Public IPv4 Address copied above into the Computer section, and click Save (under Show Options).
macOS and Linux
The domain_controller.rdp file was automatically updated to use your new domain controller's IP address during deployment, so you may use the file without further modification.
Connecting to the Domain Controller via RDP
Double-click the domain_controller.rdp file and use the following credentials to connect.
Domain Controller Admin Credentials:
- Username:
sandboxadmin - Password:
4CcXL!#X%JeU9@
We recommend that you change the sandboxadmin User’s password after logging in for maximum security.
After you log in to the instance, you can check Active Directory Users and Computers to view the default users and groups.
RDP Instance
Information
The RDP Instance is a Windows 2019 Server and comes with a default Administrator user (rdpuser) and VS Code pre-installed.
Usage
Here is how to access your newly-deployed RDP Instance:
Windows
To access your Sandbox RDP instance, start by navigating to the EC2 Console in AWS, select the Instances tab on the left, find the SandboxRDP Instance, and copy the Public IPv4 Address.
In your sandbox folder, right-click the rdp_instance.rdp file and click Edit.
Enter the IPv4 Address that you just copied in the Computer section and click Save (under Show Options).
macOS and Linux
The rdp_instance.rdp file was automatically updated to use your RDP instance's IP address during deployment, so you may use the file without further modification.
Connecting to the RDP Instance via RDP
TIP
As part of testing Xiid in a Sandbox, you'll likely want to close all inbound ports to this RDP Instance and make it only accessible via the SealedTunnel. For now, you'll need to use these credentials and traditional RDP to initially access the machine and, later, to configure the SealedTunnel.
Double-click the rdp_instance.rdp file and enter the password below to connect.
RDP Instance Admin Credentials:
- Username:
rdpuser - Password:
Cyb3r$3cur!ty
Advanced Features
Below are some advanced configuration and usage information. If you are familiar with AWS and Terraform, you can use the following information to make custom changes to the scripts to cater to your specific use case(s).
Script Configuration
You can customize the following aspects of the main.tf Terraform script to cater your infrastructure to your preferences. Below are some common modifications to the script:
- Instance Type:
- You can configure the instance types for your Domain Controller and RDP instance, if you would like faster hardware to run your sandbox domain.
- Modify the instance type on Line
97(for the Domain Controller) and Line111(for the RDP instance) to any of the Amazon Standard Instance Types. - Note: Changing the instance type may incur additional charges from AWS. Please consult the AWS Pricing Guide for more information.
- Disk Space:
- You can configure the amount of disk space provisioned for your instances.
- To change the disk space on the Domain Controller, modify the value on line
101. To modify the RDP instance disk space, modify the value on line115. - Note: Changing the amount of partitioned disk space may incur additional AWS charges.

