Technical Overview
Xiid's Zero Knowledge Networking (ZKN) products consist of a variety of components that are spread throughout different areas within and outside the enterprise network. It is helpful to understand what these components are and where they reside.
Birds-Eye View
At a high level, the technology underpinning Xiid's products can be split into four major components:
These four components work together to form the Zero Knowledge Network.
Click for a metaphorical description of Xiid's ZKN
To explain how Xiid's ZKN works from a birds-eye view, let's use the analogy of a city with multiple canals meandering in and out of the city limits.
You are a person currently outside the city (which represents a private network), wishing to access a resource within the city.
Installing Xiid's software is like building a giant, thick stone wall around the city and sealing every gate. The only remaining ways in and out of the city are narrow canals, but Xiid has modified the canals, too.
To protect the city from outside threats via the canals, all inbound traffic into the city is eliminated (all inbound ports are closed). No one is allowed to directly travel the canal to the city boundary and request to enter.
To secure the canals into the city, newly-installed metal gates in the canals (the Xiid SealedChannel and Xiid SealedTunnel solutions) make it impossible for barges or packages to directly enter the city. These gates also have specifically-shaped gaps in them, so packages with arbitrary sizes and contents (malware, etc.) physically cannot cross into the city.
Guards are stationed outside the canals' gates, and they unload and inspect the contents of the barges. These external guards are called Xiid Collectors.
In addition, the identity of every barge and package must be known and approved by the city before they will even be considered by the Xiid Collector guards. This approval process is our credential-less XOTC Authenticator. Furthermore, the identity includes the location (IP address) of who is making the request, so the city knows where to ultimately send the honored request.
If the Xiid Collectors find anything that looks extraneous, suspicious, or otherwise, that object is destroyed by tossing it into the water below before ever entering the city's walls.
In this case, a package containing your resource request is sent by you on a barge to the Xiid Collectors. After it's been inspected and approved, only the bare minimum contents of your package needed to fulfill your request are repackaged into a new shape that will fit through the specifically-shaped gaps in the metal gates at the city boundary.
Once the (many-times encrypted) repackaging of your request reaches the city border, a group of Xiid Agents on the inside of the canal gates then use the small openings in the metal gate to grab supplies from the Xiid Collectors (guards), with only the specifically-shaped packages able to pass through.
If, despite all of these processes and restrictions, a supply package still looks suspicious to an Xiid Agent, they will reject the package and it will be dumped safely outside the city walls.
Finally, once your package makes it into the city and is approved and honored, a carrier pigeon (carrying a many-times encrypted response) flies outbound from the city directly to you with your requested resource.
With this strategy, traffic is securely locked down and limited, so that only safe, secure supplies ever enter the city, and malicious actors and items and barred from entry. At no time is any direct inbound communication to the city permitted or possible if all ports are locked down.
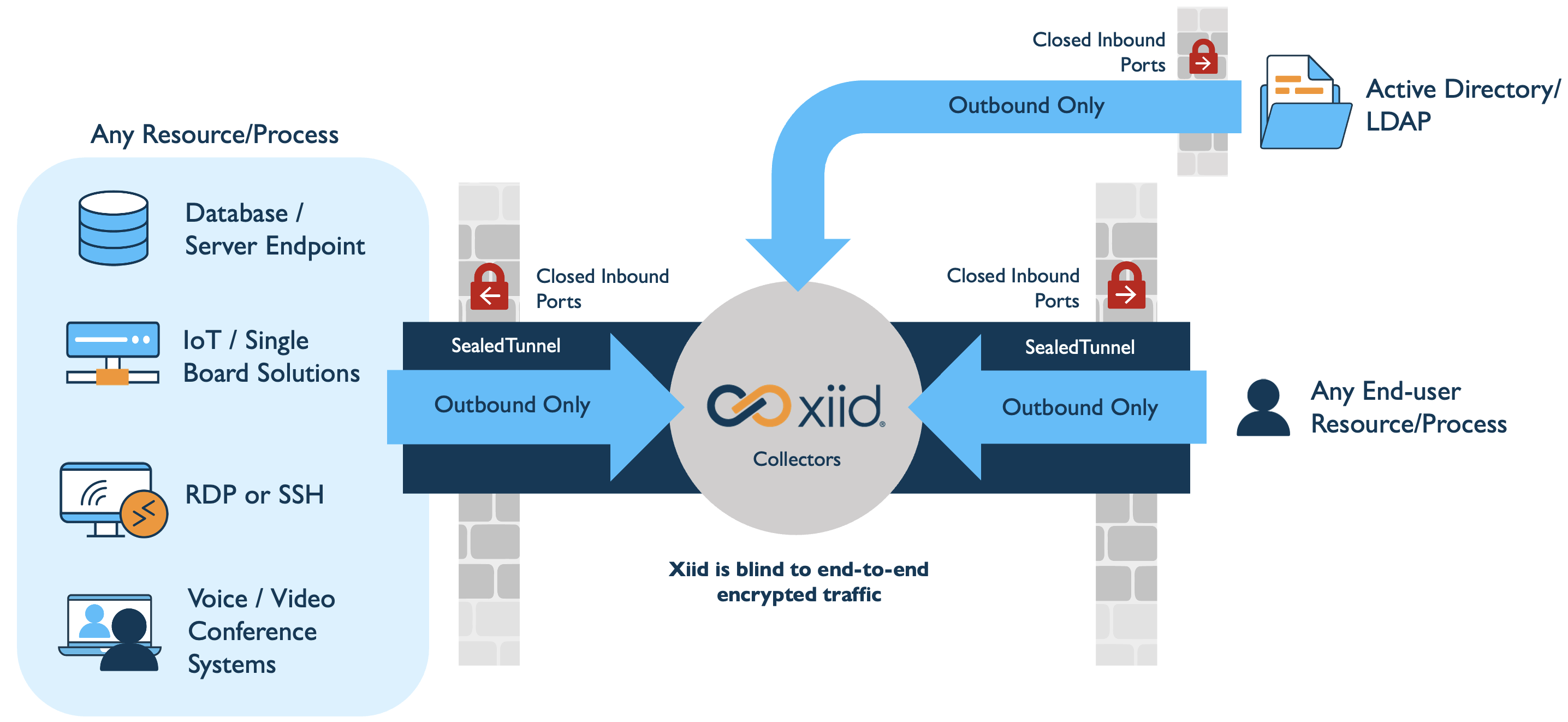
Here's a high-level diagram describing Xiid's implementation of ZKN from a more technical (and less metaphoric) perspective.
Xiid One Time Code Authenticator (XOTC™)
The Xiid One-Time-Code Authenticator (XOTC, pronounced "exotic") Authenticator, is an application which allows users to create and bind security profiles for various credentials to a credential-less one-time-code.
By default, authentication is performed using Zero Knowledge Proofs, ensuring that sensitive, stealable identity information is never transmitted across the internet.
The XOTC Authenticator is available for Android and iOS devices.
Xiid Collectors
TIP
For most deployments, Xiid Collectors are hosted and managed by Xiid as a SaaS service.
Xiid Collectors may be licensed and self-hosted for sensitive, high-risk deployments.
Xiid Request Collectors and SealedTunnel Collectors are the front-lines of Xiid's technology. Collectors are one of only two components (the XOTC Authenticator App being the other) that "reside" outside the network perimeter.
Xiid Collectors never require inbound network access to enterprise networks and all authentication data that they receive is encrypted and anonymized, ensuring that even if a Collector were to be comprised, an attacker still would be unable to access private resources.
Request Collector
Request Collectors collect requests from identity providers, convert them to our patented Smart Hybrid Protocols (SHyPs™), and place them into a queue to be picked up by an Xiid Agent. Request Collectors managed by Xiid have built-in redundancy across regions and cloud providers, top-of-the-line security, and protections at every level to minimize attack surface.
SealedTunnel Collector
SealedTunnel Collectors (STCollector) are a variation of Request Collectors that are purpose-built for the SealedTunnel product.
The STCollector operates similarly to a standard Request Collector except that it does not leverage an inner SHyPs layer, since SealedTunnels support unstructured data such as an RDP connections or web traffic. Thus, the SealedTunnel Collector does not use SHyPs to transform data before placing it in the collector's queue.
SealedChannels and SealedTunnels™
Traditionally, careful opening of inbound ports was necessary to provide access to corporate resources. This is risky, however, as open inbound ports vastly increase the attack surface of your domain.
Xiid, through its SealedChannel and SealedTunnel, are able to deliver the same levels of resource access without ever requiring open inbound ports.
SealedChannel solves this problem by creating an encrypted and secured communication channel that utilizes outbound ports and efficient, consistent polling. The messages polled from within the network are stored in memory on the Xiid Request Collector with multiple layers of strong encryption, including with Xiid's own patented technology, Smart Hybrid Protocols (SHyPs).
SHyPs are Xiid's collection of communication protocols in which only a portion of the actual protocol is known by either side (hence the word "hybrid"). The Request Collector side only understands a portion of how to encrypt the incoming requests before putting them into a queue.
Xiid Agents understand the other half of the encryption protocol and use passive transport mechanisms to only fetch the data they need. If any request wrapped in a SHyP in the queue looks suspicious, the request will be immediately discarded.
SHyPs work by leveraging the structure of data. This means that purpose-built SHyPs are made for specific types of data and cannot be used with general, unstructured data.
Layering these technologies creates a tightly locked-down communication channel through which your internal network can safely communicate with the outside world.
The SealedTunnel operates similarly to the SealedChannel but without using SHyPs, and is used for process-to-process tunneling between remote resources. The SealedTunnel, along with all Xiid software, also allows for all inbound ports to be closed and efficiently polls a SealedTunnel Collector to function.
Xiid Agents
Xiid Agents handle communication via SealedChannels and SealedTunnels.
Agents never require inbound network access and function outbound-only.
Different Xiid Agents service different types of requests and connections from Xiid Collectors:
| Agent | Function |
|---|---|
| IM | Authentication requests |
| RDP | RDP/VDI connections |
| STLink | SealedTunnel connections |
IM Agent
IM Agents are deployed on or near your directory (or Active Directory) server.
You can deploy multiple IM Agents within a single domain via Trust Relationships, and the Agents will work together to handle authentication requests.
An IM Agent can also connect to multiple directories and set up application restrictions based on your Active Directory Security Groups, for example.
RDP Agent
RDP Agents are deployed onto machines that you wish to connect to remotely, either through a direct Remote Desktop Protocol connection or to an application on the machine that you would like to access. RDP Agents function seamlessly with the STLink, wrapping RDP connections in multiple layers of encryption via the SealedTunnel.
For added security, RDP Agents randomize and cycle user passwords on each access attempt.
RDP Agents can be provisioned in the Xiid Global Management Portal.
STLink
Though not an "Agent", as it must be installed on both endpoints of a connection, the STLink acts similarly to an Agent and enables SealedTunnel connections.
STLinks can forward web traffic (HTTP/S), RDP and SSH traffic, or any other TCP/UDP data and connect to SealedTunnel Collectors.
The STLink may be deployed onto any machine you wish to connect to remotely, similarly to the RDP Agent, and is used for process-to-process, encrypted tunnelling that is sent to and from 127.X.X.X (the loopback address) and is dramatically more secure than traditional RDP or VPNs. Only outbound port 443 is required for it to function.

