Zero Knowledge Networking Introduction
Increased risk of cyberattacks on the enterprise network and cloud-connected users is proving to be more difficult than ever, despite the rise of Zero Trust.
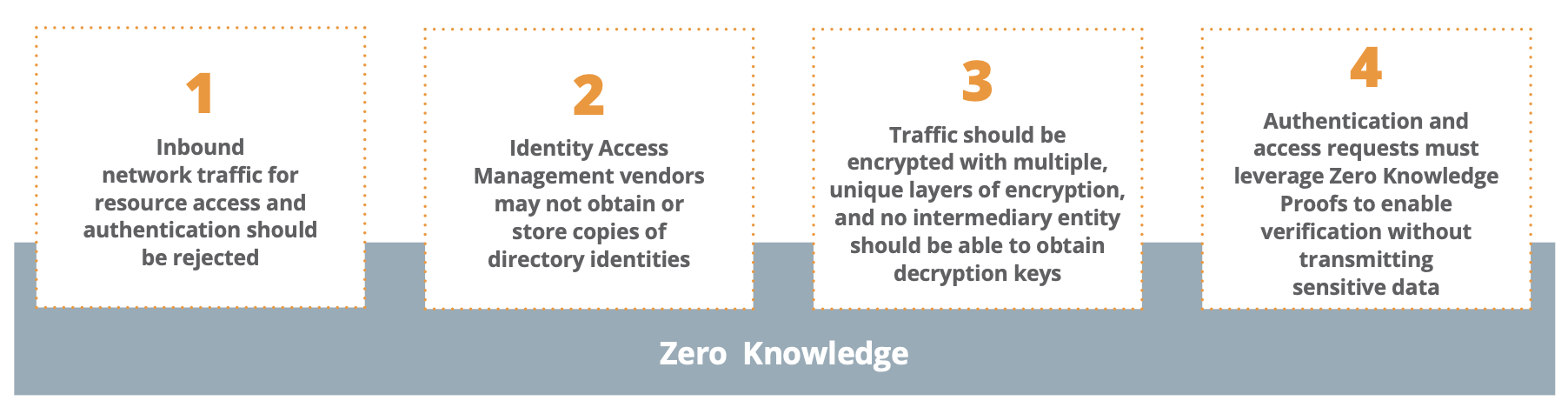
Xiid's Zero Knowledge Networking (ZKN) is a new networking architecture that meets and vastly exceeds the NIST Zero Trust Tenets through the following:
- All parties – including endpoints and the Zero Trust vendor in-between – are guaranteed to have no excessive knowledge of each other’s sensitive data or location
- Open inbound ports are never used, eliminating network attack surface
- All traffic is wrapped in multiple layers of encryption
- Zero Knowledge Proofs authenticate users without transmitting sensitive information or credentials
This documentation describes the installation, configuration, and operation of Xiid's product offerings, as well as a guide for deploying a sandbox environment that can be used for testing and to gain familiarity with Xiid.
Xiid Products
| Product | Description |
|---|---|
| Identity Access Management (IM) | Xiid's in-house Identity Access Management solution is credential-less and uses Zero Knowledge Proofs to authenticate users. Unlimited numbers of easy-to-use Xiid-provided SSO portals may be provisioned. Trust Relationships allow external users easily-revokable access to specific resources without needing to onboard them to your domain. Xiid never stores directory identities but provides the same level of functionality as traditional federated identity providers. |
| SealedTunnel™ (ST) | SealedTunnel™, Xiid's resource access solution, are triple-encrypted, outbound-only secure tunnels. Backed by Xiid IM and optimized at the lowest levels of the OSI model, any type of internet traffic can be wrapped and secured. Resources located anywhere in the world can connect without ever needing to accept inbound network traffic or even having public IP addresses. |
More Information
For more information on Zero Knowledge Networking, read our seminal whitepaper.
If you're looking for information on how Xiid conforms to and exceeds NIST's Zero Trust Tenets, check out our NIST compliance guide.

