IM Components
Each component of Xiid IM serves a key role in enabling Xiid's comprehensive Zero Knowledge Networking Identity Access Management (IM) solution. Understanding the function of each of these components individually will help system administrators better manage and interact with the Xiid ecosystem.
Request Collector
DANGER
Because it is addressable, a Request Collector should never be located on the same network as your directory service. We recommend that your directory service be segmented and isolated to its own subnetwork.
Request Collectors are the front lines of Xiid's Zero Knowledge Networking Architecture and are the only component within Xiid’s architecture that allows external, inbound communication over inbound Port 443.
The Request Collector collects authentication requests and puts them into a queue which is then consumed by an Xiid Agent. The response from the Agent is forwarded back through the Request Collector using Perfect Forward Secrecy. Each Collector can support thousands of requests per second.
All code for the Request Collector is compiled to binary and uses no third-party libraries. Data from requests is never stored on disk, and all data flowing through the Collector is encrypted end-to-end where the Collector is never one of the "ends".
Xiid-vended Requests Collectors are available as a SaaS service, securely managed on Xiid’s infrastructure and distributed across multiple regions and cloud providers.
Although not needed in most cases, a Collector can be self-deployed instead for extremely sensitive use cases.
SealedChannel
The Xiid SealedChannel is a one-way communications channel that is established between an Xiid IM Agent and an Xiid Request Collector.
When an Xiid Agent is set up, a code is provided to the Agent which allows the Agent to reach out to the Request Collector to establish the communications channel.
After the connection has been established, authentication requests will be accepted by the Request Collector. Next, those requests are repackaged into Xiid's patented Smart Hybrid Protocols (SHyPs) that only physically allow for the bare minimum, encrypted information necessary to fulfill an authentication request, eliminating the risk of malicious code injection.
Finally, the request, packaged into SHyPs, is put into the Request Collector's queue to be picked up and serviced by the proper Xiid Agent.
XOTC Authenticator
The Xiid One Time Code (XOTC) Authenticator, a key piece of Xiid's Zero Knowledge Networking approach, is a highly-secure, one-time-code-based authenticator that uses Zero Knowledge Proofs to authenticate users rather than traditional credentials.
Users scan a QR code with the XOTC Mobile Application to log in to SSO Portals and access their resources.
No sensitive identity information is ever transmitted over the internet and stealable, and the absence of traditional credentials rebuffs phishing attempts.
Requests via XOTC are wrapped in multiple layers of encryption and a patented protocol, SHyPs, over the SealedChannel.
Additionally, codes are bound to singular browser sessions, so interception and replay of a code in a Man-in-the-Middle (MITM) Attack would not enable an attacker to authenticate themselves on a victim's behalf.
Agents
An Xiid Agent is a light, intermediary piece of software that acts as the liaison between the Request Collector and your internal resources. Through the use of Agents, inbound ports on your network can be closed.
An Agent pulls requests, outbound-only, from the Request Collector queue and takes appropriate action depending on the type of Xiid Agent. Agents reside in the same network segment as the resource with which the Agent interacts.
Xiid highly recommends using proper network segmentation to, at a minimum, separate your resources by subnets, with Xiid Agents handling communication between subnets.
IM Agent
The IM Agent resides in the same subnet as your directory and provides the Agent Configuration Portal and liaison to your directory for servicing authentication requests.
Importantly, the IM Agent handles all authentication interactions with your directory and moderates access to and vends SSO portals.
Through its Agent Configuration Portal, it allows for configuration of multiple directories, setting up Authenticators, Firewalls, Translators, and Trust Relationships, and configuring your Xiid SSO Portals, including the Applications that should be available through them.
Additionally, this portal is used to configure SealedTunnel.
The Active Directory Agent is part of the core of Xiid's software stack, as almost all interactions with the enterprise network flow through this Agent, either directly or indirectly.
Xiid RDP Agent
The RDP Agent runs on machines that you would like to RDP into. The Xiid RDP Agent runs in the background on the machine and manages the credentials used for authentication on the machine through an RDP connection.
When a user attempts to RDP into a machine through an Xiid SSO Portal, the RDP Agent cycles the user's password on the remote machine and pushes this one-time password back out to the client's computer, where it is injected into the user's clipboard.
When the .rdp connection file is downloaded from the SSO Portal, the username will already be provided, and the user can paste the password into the prompt to sign in.
As soon as sign in is completed, the user's password is rotated again by the Agent to a new one-time password, reducing the risk of breach if the first password was intercepted.
SSO Portals
Xiid's easy-to-use SSO Portals allow users easy access to the resources they need, which include SaaS applications, SAML2.0 applications, RDP/VDI, internal applications, and remote access to any resource over the SealedTunnel.
Xiid allows system administrators to set up an unlimited number of SSO Portals for different groups of users.
When you create a new SSO Portal, you can specify an ID which will be used in the SSO Portal's URL.
It is recommended that, at a minimum, system administrators set up SSO Portals that correspond to directory Security Groups that reflect different permission levels, such as an SSO Portal for IT with specific RDP access to remote machines on the network that should not be accessible to other users in the domain.
Applications
Xiid Applications allow System Administrators to integrate various external applications into SSO Portals.
For each application that you would like to provide access to, you can create an Application Component within the Xiid IM Agent defining how to integrate with the external application.
Xiid currently supports 5 types of applications: RDP, RDP Apps (VDI), Microsoft 365, Google Workspace, and any external application that supports SAML2.0 authentication.
When configuring Xiid Applications, you can specify which SSO Portal(s) the application will be available through.
Authenticators
Xiid Authenticators connect IM Agents to LDAP Directories, including Active Directory, and underpin the XOTC Authenticator and other methods of authenticating supported by Xiid.
They are also used to separate SSO Portals and Applications by Security Groups within those directories. For each Security Group, you can create an Authenticator to your LDAP Directory with specified included Security Groups (to grant access to specified SSO Portals) as well as excluded Security Groups (to deny access to specified SSO Portals).
You may create an unlimited number of Authenticators with any number of connections to any number of LDAP Directory Services within the same subnet as the IM Agent.
Secondary Authentication
Xiid supports legacy 2-Factor Authentication for accessing Single Sign-On Portals, as well as methods such as YubiKeys and CAC/PIV cards.
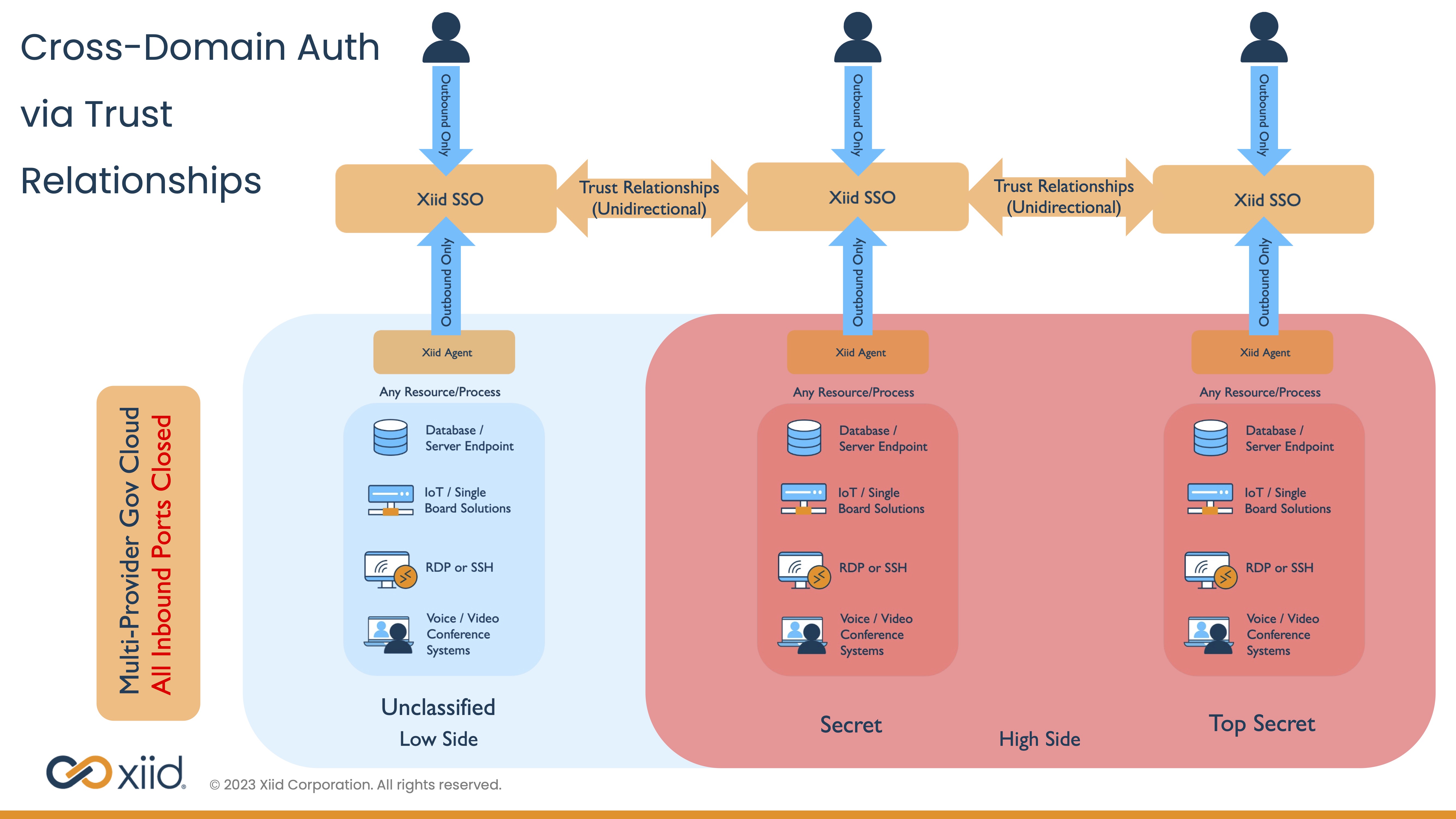
Trust Relationships
Virtual Trust Relationships make it easy to share resources between separate domains, unidirectionally, without making modifications to any directories.
Virtual Trust Relationships allow System Adminstrators to create ephemeral "Trust Relationships" between domains and share specific SSO portals and applications between them.
For instance, this could be used in a multi-provider government cloud environment to allow users logged into a "high-side" SSO portal access to specific resources on the "low-side" without having to switch devices or re-authenticate:
Firewalls
TIP
This Firewall component is an additional layer of security and control provided by Xiid, and is not a substitute for an enterprise firewall. When it comes to your enterprise network firewall, Xiid always recommends closing all inbound ports and access.
Xiid’s Firewall component allows administrators to add IP addresses to Allow or Deny lists, allowing communications that need to happen while blocking potential risks.
The IM Agent will accept or deny any attempts to authenticate based on the lists configured. If a user attempts to sign in from a denied IP address, the authentication request will be ignored by Xiid.
Users can create and use as many Xiid Firewalls as they see fit to secure their connections in different circumstances.
Translators
Translators are an exceptionally powerful feature that allow administrators to convert incoming authentication requests into particular formats for the local domain.
You can choose to convert domains, usernames, or User Principle Names (UPN) to something that can be understood by the directory service locally.
For instance, if an employee uses their email address for authentication, such as user@example.com, but the Active Directory Service uses a local domain name, such as example.local, you can configure a domain translator to translate example.com to example.local when querying the directory.
This could also be leveraged to increase obfuscation of usernames across the network.

