Product Offerings
Xiid offers multiple software technologies for securely accessing enterprise resources. Management of Xiid technologies may occur at multiple professional levels from system administrators to individual users. Consequently, Xiid offers multiple applications and portals to help users configure and manage their applications, domains, directories, authentication, users, machines, data, and more.
Xiid Products
Below is a high-level description of Xiid’s products. The cornerstone of Xiid’s products is the Xiid.IM solution which provides state-of-the-art identity and access management and security. Xiid’s additional product offerings are built on top of Xiid.IM to provide additional access to your private network’s resources using the certainty of the accessor’s identity.
Critically, all of Xiid’s products function without requiring any inbound ports to be open on your private network.
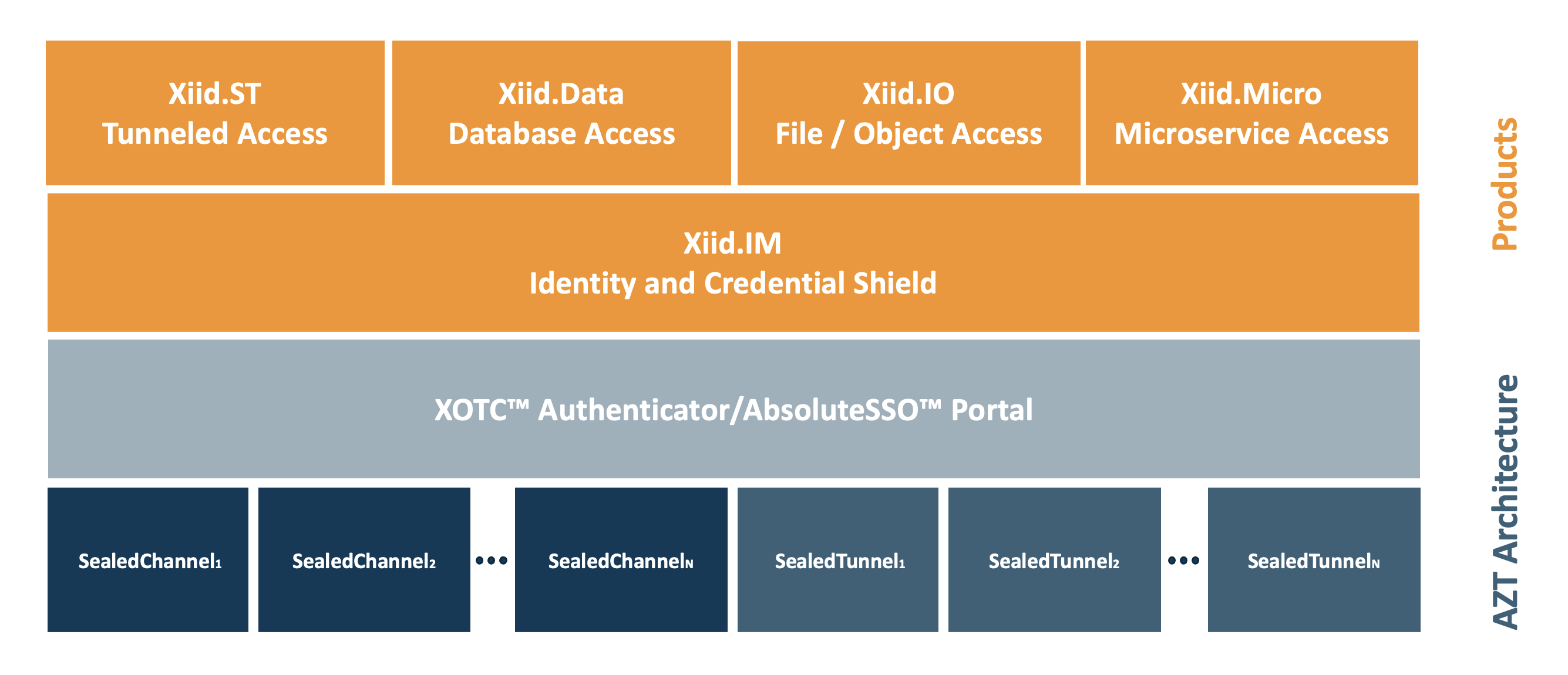
Xiid.IM V3 Identity and Credential Shield
Available Now!
Identity Access Management & SSO for Cloud and Hybrid-Cloud, SaaS Delivery
No credential harvesting with XOTC Authentication
No changes to AD or copying outside network perimeter
No malicious code and ransomware payload injection
Additional AZT™ Products
Xiid.ST - AbsoluteZero Trust™ SealedTunnel™ tunneling
Xiid.ST (SealedTunnel™), backed by Xiid.IM, replaces legacy VPN and VDI solutions while improving security posture, reducing administration complexity and operating costs, and enhancing the user experience. Xiid.ST provides process-to-process tunneling between remote resources without requiring any open inbound ports on either resource. It also can be deployed for connectivity to remote autonomous devices, and to secure high-stakes SSH connections. Xiid.ST supports VDI (RDP, SSH, X11, Wayland, etc.) or any IP communication (TCP, UDP, BGP, ICMP, etc.).
Xiid.Data - AbsoluteZero Trust™ database access
Utilizing Xiid.IM and both passive and encrypted JSON data formats, Xiid.Data delivers secure database queries and responses using SealedChannel™/SHyPs. Enterprise data is never cloned on-premises or in the cloud.
Xiid.IO - AbsoluteZero Trust™ file and object access
Xiid.IO leverages Xiid.IM to bring unstructured access to data residing on-premises or in the cloud under the protection of the AZT™ architecture. As with all AZT™ products, data is never cloned or replicated anywhere to achieve access.
Xiid.Micro - AbsoluteZero Trust™ microservice to microservice access
Xiid.Micro enables secure communication among microservices inside the network perimeter and in the cloud. A range of microservices are supported including those that support RESTful APIs, RPC protocols, and others.